Use-cases
Address Labels, Fund Flows & Graphs: BlockSec Builds a Crypto Risk Control System with NebulaGraph
The EU’s MiCA Act and OFAC Sanctions are raising the bar for crypto risk control. How can we build secure, compliant systems in this new era? BlockSec, a global leader in blockchain security, offers a solution: a robust risk control system built on NebulaGraph, enabling seamless flow from data ingestion to actionable risk insights. Yunfei Xie, a security R&D engineer at BlockSec, leads work on crypto address tagging and graph databases.
The Core Idea: From Transaction Data to a Risk Network
The Atomic Unit: The Transfer as the Core of Fund Flow
All complex on-chain value transfer activities are ultimately reduced to the most basic token transfer.
However, the raw on-chain data is incredibly complex, including batch processing of multiple transfers, complex swap logic, and cross-chain messaging.
Our goal is to build a foundation for risk analysis from these massive and complex on-chain “atomic units”, including noise filtering (such as removing junk tokens) and the establishment of a Fund Flow Graph.
Risk Network: The Graph is the Skeleton, Labels are the Soul
Imagine you have only raw blockchain data: connections between anonymous addresses, such as the transfer from “0x098b…2f96” to “0x1361…1f39” and then to “0xd90e…f31b.” This data forms an “anonymous skeleton”—we see structured connections but lack meaningful context. We know funds are flowing, but we don’t know who’s moving them, why, or what they represent.
When we assign labels to these addresses and transactions, the data comes to life.
For example, by labeling “0x098b…2f96” and “0x1361…1f39” as “Lazarus Group: Ronin Bridge Exploiter,” and “0xd90e…f31b” as “Tornado.Cash Router,” we can clearly see that the renowned North Korean hacker group, the Lazarus Group, laundered 3,000 ether through the sanctioned mixer Tornado.Cash after the Ronin Bridge attack.
Through labeling, the anonymous skeleton becomes an insightful risk map. Labeling gives meaning to the data, allowing us to accurately identify high-risk entities and behaviors from massive amounts of on-chain data.
Accurate Portrait: On-Chain Risk Classification System
By combining graph analysis with a sophisticated tagging system, we can accurately profile on-chain risks. The system needs to be able to identify and tag multiple threat types to help us fully understand and respond to the “dark forest” of the crypto world.
As shown in the following figure:
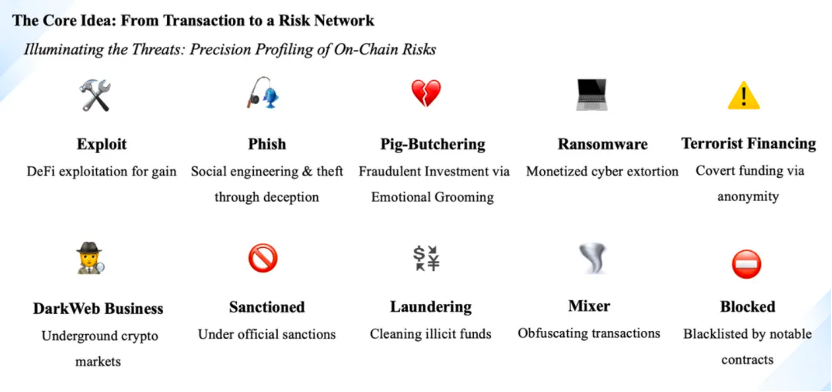
By accurately identifying and classifying these threats, the risk control system can provide multi-dimensional risk assessment.
The Implementation: Building the Risk Control System with NebulaGraph
Reasons for Choosing NebulaGraph
First and foremost, performance was the primary consideration. NebulaGraph’s distributed architecture and superior concurrent processing capabilities can easily handle queries on tens of billions of nodes and edges, ensuring we complete complex graph traversals and analyses in milliseconds.
Secondly, a flexible data model allows us to better depict the complex relationships in the blockchain world. The property graph model in NebulaGraph is ideally suited to capture the rich, multi-layered connections in blockchain data.
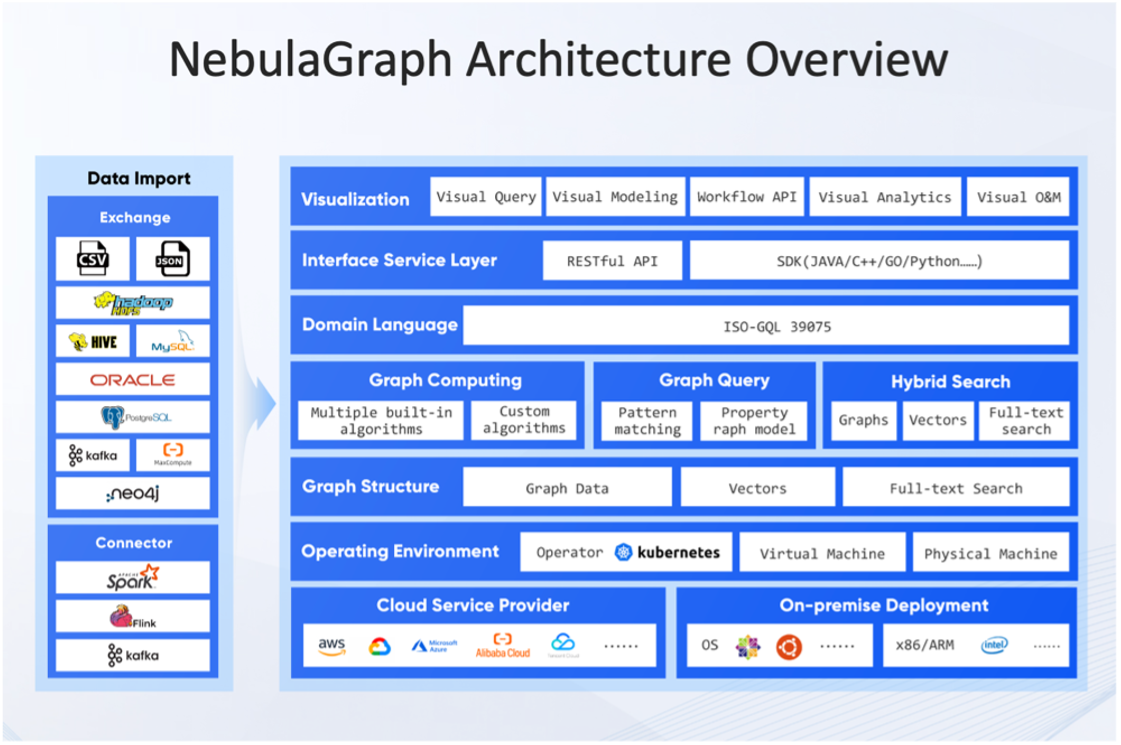
Finally, ecosystem compatibility is also a key consideration. NebulaGraph natively supports ISO-GQL, which reduces the learning curve for our team. Its rich visualization tools and APIs allow us to quickly build intuitive cash flow analysis interfaces.
The Value of Risk Control Systems
Proactive Prevention: Building a Proactive Defense System
Core Capability: Real-time blocking of risky transactions.
Application Scenario: When processing user deposits on an exchange or interactions on a DeFi protocol, an API call can fetch the risk score of associated addresses. If the score exceeds a threshold (e.g., funds from a mixer or sanctioned entity), the system can automatically halt or reject the transaction, stopping the risk at the gate.
In-Process Control: Raising the Security Baseline of Partners
Core Capability: Comprehensive due diligence on counterparties and projects.
Application Scenario: When evaluating a new DeFi project for integration or conducting a large transaction with an institution, graph analysis can review the historical behavior and funding network of their contracts and wallets. This effectively identifies if they have close ties to "high-risk entities," providing critical data for partnership decisions.
Post-Mortem Forensics: Providing Precise Investigation & Evidence
Core Capability: Deep penetration and tracing of on-chain funds.
Application Scenario: After a security incident (like a hack), provide clear, visual fund flow reports for the project team and law enforcement. Our system can quickly trace the complete path of stolen funds through multiple hops, mixers, and into exchanges, securing the crucial time window for asset freezing and recovery.
Conclusion: Seeing the Hidden Patterns in Web3 Security
By leveraging NebulaGraph, a high-performance distributed graph database, BlockSec has built a scalable and real-time risk control system capable of mapping complex on-chain relationships across billions of transactions.
The system transforms raw blockchain data into a dynamic fund flow graph, where advanced graph traversal and analysis enable precise tracking of high-risk activities. With NebulaGraph’s low-latency queries and flexible property graph model, BlockSec efficiently integrates address labels, threat intelligence, and algorithms to identify malicious behavior, trace stolen funds, and assess risk in real time.
This technical foundation powers capabilities like transaction screening, counterparty due diligence, and post-incident fund tracing — proving that in the world of blockchain security, graph technology is necessary.